Threat and Vulnerability Observation System
TaVoS
We offer suitable TaVoS editions for different purposes and target groups. From easy-to-use online tools to comprehensive software for scanning security vulnerabilities on your private PC, to professional use in companies with the Pro Edition.
Compare
TaVoS Editions
Whether end user, Information Security Officer in an SME, or security-aware user.
There is a suitable version for everyone.
Easy to Use
 Details
Details

TaVoS Desktop
Monitoring of locally installed software for known security holes and vulnerabilities for each Windows PC
- Local monitoring
- Dashboard
- Signature update
- Easy to use
Professional
 Details
Details

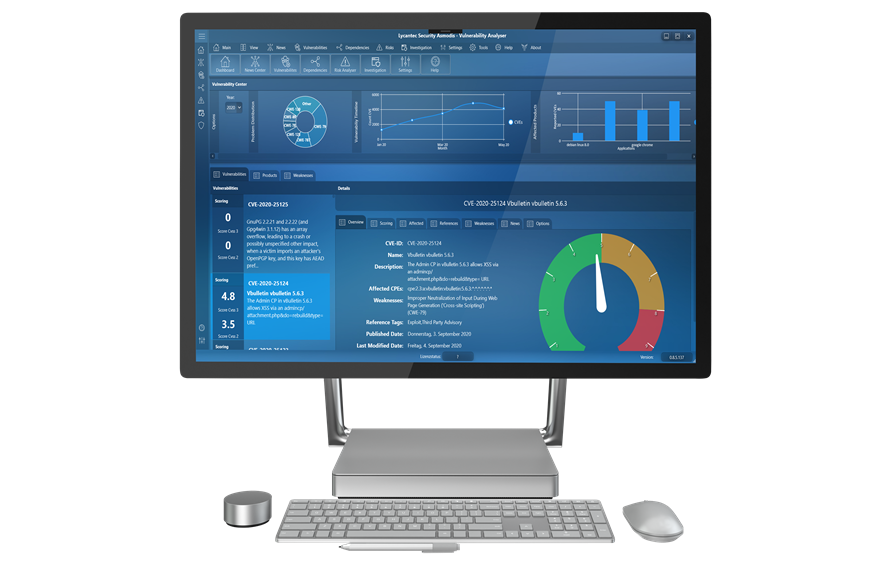
TaVoS Pro
Comprehensive solution for companies in the areas of post-market surveillance, risk management, dependency check, and searches.
- News Center
- Dependency Manager
- Alert Hub
- Vulnerability Center
- Investigations Module
- Risk analyser
Quick
 Details
Details

TaVoS Web
A user-friendly solution to check for known security vulnerabilities and other security-related online tools on your own websites.
- Web Security Scan
- Software Vulnerability Research
- E-Mail Check










